End-to-end encryption (end-to-end encryption or E2EE) is a security feature that protects data during a message exchange, so that the content can only be accessed at both ends of the communication: the sender and the recipient. Currently used in applications such as Telegram and WhatsApp, the tool is an implementation of asymmetric encryption and ensures that information is not intercepted. No one but those involved in the conversation should have access to the content transmitted through end-to-end encryption, not even the app companies.
Although most users do not question the feature, the subject has received special interest since last Sunday (9), when the site The intercept posted messages exchanged by the current Minister of Justice, Srgio Moro, and the prosecutor of the Public Ministry in Curitiba, Deltan Dallagnol, through the Telegram application. The content released by the vehicle suggests that then Judge Moro would have had antithetical conduct when collaborating in the investigations of Operation Lava Jato. It is still unclear how the information was obtained.
Telegram Conversation Leak? Understand Messenger Privacy

Telegram X Secret Chat Main Menu Photo: Raquel Freire / dnetc
Want to buy a cell phone, TV and other discounted products? Meet the Compare dnetc
Wanted by dnetc, the Telegram application, known for security features, with secret conversations and E2EE, ensured that data was not stolen from their servers. In theory, this would not be possible, since secret chat protects information in transit because of its end-to-end encryption. But how does this technology work anyway?
To begin with, encryption is the name given to mechanisms that transform information that was transparent into something that cannot be understood by an external agent. An encryption key used with the algorithm to scramble messages, so that it is impossible for an intermediary who has access to them to understand the content. Therefore, the information is encoded. To make the text understandable again, you must have correct key access.
This way, only the person holding the key can see the original data. The key is a very long sequence of numbers generated by the software, either a messaging app or an e-commerce service protecting credit card data. There are two types of encryption: symmetric and asymmetric. End-to-end encryption is an implementation of asymmetric.

WhatsApp launches end-to-end encryption in April Photo: Luciana Maline / dnetc
Symmetric and asymmetric encryption
In symmetric encryption, the most common, only one key needs to be applied to encrypt the message at one end and to retrieve it at the other. This type of encryption was used in messages during World War II, for example. The key is a type of code that allows you to reconstruct the original message.
The two most widely used protocols for data protection on the Internet, Secure Sockets Layer (SSL) and Transport Layer Security (TLS), use symmetric encryption to protect both transmitted and stored data. Symmetric encryption, however, can present a problem, as both ends of the information must have the same key, which may involve sending it back and forth, risking interception. Therefore, it is not effective in all cases.
When you want more security in exchanges, the solution is asymmetric encryption. In it, two types of keys are used for each end of the communication, a public key and a private key. Public keys are available to both parties and to anyone else, in fact, because everyone shares their public keys before communication. Each person has a pair of keys, which are complementary.
So if, for example, Peter wants to send messages to Joan in an end-to-end encryption application, he will use Joan's public key to encrypt the message. The content can only be decrypted using this public key (from Joan) next to her private key, which not even Peter has access to. This private key is the only element that makes it impossible for any other agent to decrypt the message as it need not be shared.
End-to-end encryption, as the name suggests, protects data so that it can only be read at both ends of the process by the sender and the recipient. In theory, no one else can read encrypted data, including hackers, governments, and even the server through which the data is sent.
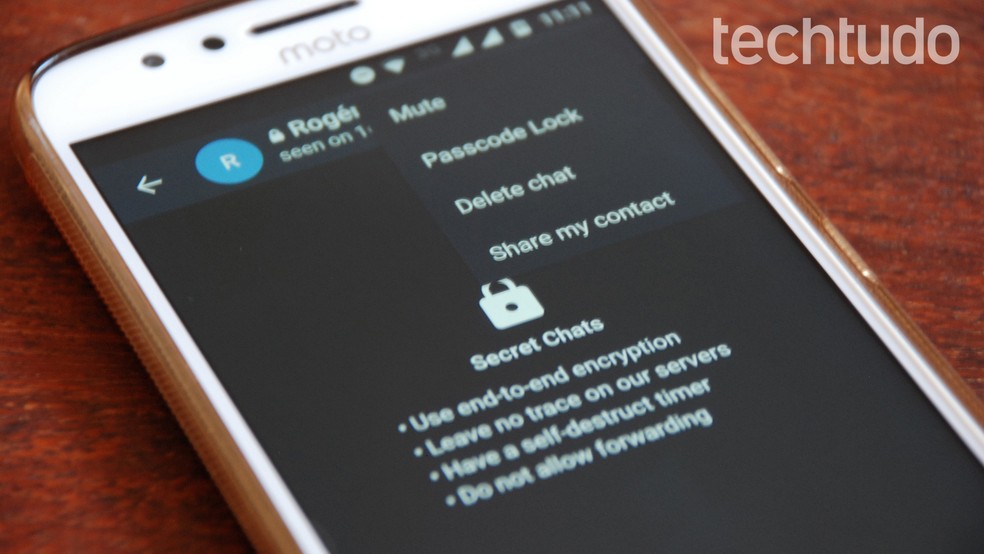
Telegram X Secret Chats on Android Photo: Raquel Freire / dnetc
Thus, security technology protects not only users, but also companies, who cannot be pressured by authorities to deliver private information because they do not have it on their servers. End-to-end encryption, however, does not guarantee that information will not be accessed if a hacker has access to the user's device or hacks into their account. The feature protects only the content submission process and ensures that it is not read when intercepted on submission.
End-to-end encryption does not depend on a user action. It is used as a feature of applications and software and all automated by services. In addition to Telegram and WhatsApp, iMessage uses this type of encryption, as do Skype and email services such as ProtonMail and Microsoft Outlook. A disadvantage of E2EE algorithms is that they are usually slower than symmetric methods but each day this difference becomes less relevant.
Telegram Conversation Leak
Telegram has gained a reputation for selling itself as safer than competition and the app was one of the first to offer end-to-end encryption. However, it is important to note that this type of protection is only available in secret chat. Taking into account the software protections, Telegram raises two possibilities for the leak of conversation between Moro and Dallagnol. One of these involves account hijacking and history recovery on an unauthorized device. The vulnerability could also be in the user's mobile phone, possibly infected with malware: No application can protect your information if the device itself is compromised, the company says.
Telegram: Four Curious Functions
