As the extremely complex subject, I called my friend and security expert Alberto Azevedo to tell you the size of the drama.
If you want to know a little better, check out the video we made at Campus Party of Pato Branco – PR at the end of the year step:

The world panicked this week. The simple reason has come to the public two extremely serious vulnerabilities that affect virtually (virtually) every processor in use in the world!
As soon as the information was released, even more "perplexing" others arrived. The first was that the failure had already been reported to manufacturers no less than SIX months and the second that Brian Krzanich, CEO of Intel, "rudely" sold no less than HALF of his shares, keeping as little as he could. I could legally stay when I learned of the flaws a few months ago.
The reason manufacturers have known this for so long and done nothing (and Brian Krzanich did what it did) is simple: The failures, and especially their impacts and difficulties in the correction process, They are much more serious than you can imagine.
Starting at the beginning
The year was 1946 and a Hungarian mathematician named John von Neumann, with his research team at the Princeton Institute for Advanced Studies (IAS), developed a new computational model where a digital machine could store its programs in the same memory space as the data. , thus being able to manipulate such programs. This solved a number of limitations that the fixed model, adopted so far, has. That's because computers were not so 'programmable' until then, but practically 'designed' for the function they were designed for. Schematic drawings of how he would do it were written, it was written, and that's it.
It would be as if you created a "chocolate cake making" computer, it would have the unique and unique ability to make chocolate cake for life. If you wanted to change that, or "teach" him how to do a new type of coverage, you would face an extremely painful process that would have to redesign the machine as a whole, and could take weeks to create a new program at ENIAC and come back. to work.
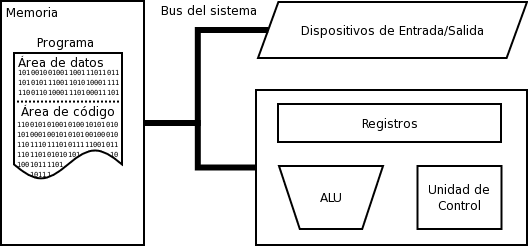
Von Neumann's model was revolutionary, radically changing the way things were done and creating countless new possibilities for computing. It enables the machine to handle received instructions and this is the ability to treat instructions as data which makes assemblers, compilers and other automated programming tools possible.
It was amazing!
However, there were problems and criticism, the first and most obvious time was the bottleneck. The data transmission channel between the CPU and memory leads to what is known as the "von Neumann bottleneck". Limited data exchange (throughput) between the CPU and memory in relation to the amount of memory has been problematic since that time.
On most modern computers, the data exchange between the processor and memory is much less than the rate at which the processor can work. This seriously limits the processing speed, which could be much more efficient, especially when the processor required to process large amounts of data. The CPU is constantly forced to wait for data that needs to be transferred to or from memory. Because CPU speed and memory size have increased much faster than the throughput between them, the bottleneck has become yet another problem, a problem whose severity increases with each CPU generation. Since programs are being stored in the same space as data, changing the program can be extremely harmful, either by accident or a design flaw, a faulty program can change other programs or even the operating system. Several mathematicians, including Alan Turing, opposed Von Neumann's model by pointing out the mathematical flaws in the process and wrote articles proposing other models, but Neumann's involvement in the Manhattan project and ENIAC project made his conception for EDVAC larger. circulation, and the rest history.
Getting back to the current processor problem
I'm not blaming von Neumann for today's failure, the culprits are the hundreds of engineers who came later and didn't have the heart to do what they'll have to do now. A complete redesign and architecture restructuring in the face of the new challenges and reality of current computing. This is because (spoiler alert!) The vulnerability that was named Specter, at first, simply cannot be fixed with a patch !!!
It will require a redesign of the processors. Do you understand, dear reader?
Virtually everyone, I repeat, ALL the processors in use in the world today need to be EXCHANGED !!!! Do you understand why the deepest rabbit hole? Do you understand why manufacturers have done nothing so far, even though they have had six months to do? Well, Brian did, sold every action he could, because he knew months ago what the world knew now. See, there is no production capacity to make the changes that need to be made. The subject is very serious.
Before we continue, let's explore and quickly explain the issues.
The problems
Months ago some independent security researchers and others within the Google Project Zero project discovered two vulnerabilities in processors that were called Meltdown and Specter. They allow malicious attackers to steal / access the entire memory contents of computers, cell phones, and servers. The first, called Meltdown, is limited to Intel processors and breaks the isolation between user applications and the operating system. You can find more information here, besides seeing a PoC here and here.
For this vulnerability there are some patch patches that are already being made available, but they will cause a reduction in processing power that could range from 5% to 30%. While it will be a bit of a nuisance for end users to lose about 30% of their station's processing capacity, do you, dear reader, have any idea of the financial impact this has on an Amazon for example?
Amazon, Microsoft, Google, among other major players in the cloud market, will be harmed astronomical Because suddenly your computer park simply won't accommodate the use that is being made of it anymore. Note that while on your computer, an attacker may steal information from you, on a virtualized server it may steal information from all the people / companies that are hosted on that virtualizer. We're talking about passwords, data, encryption keys, anything.
Now note that the patch patch, although it exists for the Meltdown case, needs to be applied by every system administrator on earth in your operating system. Remember WannaCry? That vulnerability was discovered and there was a patch available for months in Windows.
Do you understand the problem?
Worse than Meltdown can be exploited by any script-kiddie with access to a computer and two functional neurons.
About Specter …
Luckily the exploration of the most complex Specter to perform is, and I say lucky, because as has been said, theoretically there is simply no possible fix for vulnerability. It will require a complete redesign of the processors and Intel, AMD and ARM would have to do a recall complete of all processors already manufactured, in practice the problems will be solved only in the next hardware life cycle, meaning we will feel the effects for the next decade. Basically what happened is that in Asia and war for performance and capacity, manufacturers have become sloppy with safety. It is not today that this is questioned by security researchers worldwide. So much so that many mission-critical equipment is equipped with so-called safe processors. Processors made by companies like Kryptus, a strategic national defense company owned by friends Gallo and Henrique and their Secure Crypto-processor (SCuP) or Secure Processors, manufactured by Broadcom for example. The Specter was named that way because it exploits what we call "speculative processor execution capability."
Modern processors use techniques like branch prediction and speculative execution to maximize performance. Remember Von Neumann's bottleneck? These are some of the techniques adopted to try to mitigate this problem. In practice if the data destination of a branch Depending on data that is still being read into memory, the CPU will try to "speculate" (guess / predict) what this destination is and run ahead. When the data actually arrives, she will confirm or discard this prediction. The attack consists in abusing this speculative capacity of the processors and inducing the victim to perform operations that would not normally occur, which leads to information leaking via side-channel.
You can see an example implementation here. Although it is possible to mitigate the effects of the Specter via micro code, the solution will only occur through a redesign of processors, which absolutely does not occur quickly.
The problem is that in the war between safety and speed, compromises were being made in the name of performance. The bill is coming now.
Finishing
In the end this incident can bring positive results. The first must be a profound reflection on the market and the danger of being dependent on so few hardware vendors, see, the processor market is literally in the hands of three companies. We are totally dependent on them, their wishes and their decisions. Another benefit will be greater attention and importance to be given to safety issues. This old dilemma, Safety x Speed.
"If you have a chest, putting a lock on it makes it safer, but it will take longer to open and close it every time you need to do it during the day."
And in this discussion to this day, performance has always beaten security, it might change a little now. Another advantage will be the fact that technologies such as Field-Programmable Gate Array (FPGA) and Complex Programmable Logic Device (CPLD) should gain more relevance as they have much more features and customization possibilities than technologies in use today. In short, the solution will not be simple Intel is clearly trying to calm the mood, but the question is very serious. As has been said, Meltdown can be exploited even by my five-year-old daughter, as Specter can be exploited by, or sponsored by, more qualified state personnel. Which raises the question: How long have you thought the NSA, for example, could be exploiting these flaws secretly? Now think about it.
Even if manufacturers were willing to go bankrupt to try to do so in record time, this technology has not yet been created, as a complete design of a new processor can take years, and we have no production capacity for this volume.
Can you understand now why the manufacturers did not do anything very concrete in these six months of knowing about the flaws? Can you understand the implications of all this?
Welcome to Cybergeddon!
Thanks
I would like to express my compliments and thanks to Alberto J. Azevedo for the clear and achievable approach. You can read some articles that he eventually publishes. on MediumFrom now on, expect to see some of his content here on the blog either copyrighted or co-written.
See you next time!
_____________________________________________________________________________
See an error or would you like to add any suggestions to this article? Collaborate, click here.
