A new banking virus has been attacking corporate clients of financial institutions in Brazil. CamuBot, as the malware is called, camouflages itself as a security module required by the attacked bank and tricks the victim into stealing his bank credentials.
The first malware activity was detected last month and the disclosure was made by IBM X-Force researchers last Tuesday (4). Since then, criminals have directed attacks on both private companies and public organizations. Unlike most banking Trojans, CamuBot does not hide in the system. The virus, in addition to using the bank's logo, has the same appearance as an internet banking, leading the victim to believe that he is installing an official application.

CamuBot virus uses sophisticated scheme to steal bank data in Brazil Photo: Pond5
Want to buy cell phones, TV and other discounted products? Meet Compare dnetc
According to the researchers, CamuBot is much more sophisticated than the malware used in fraud schemes in the country until then. Instead of simple fake screens and a remote access tool, CamuBot's tactics resemble those used by malware manufactured in Eastern Europe, such as TrickBot, Dridex or QakBot, experts explain in a post on the IBM website.
Understand how the attack works
The scam involves quite complex social engineering tools. Initially, CamuBot operators identify, through a basic survey, companies that do business with the targeted banking institution. Then they call the person who would likely have the company's bank account credentials.
By posing as bank employees, criminals trick the victim into visiting a fake website to check if the security module is up to date. As part of the trap, the validity check appears negative, and operators of the virus indicate downloading and installing a new module to solve the problem.
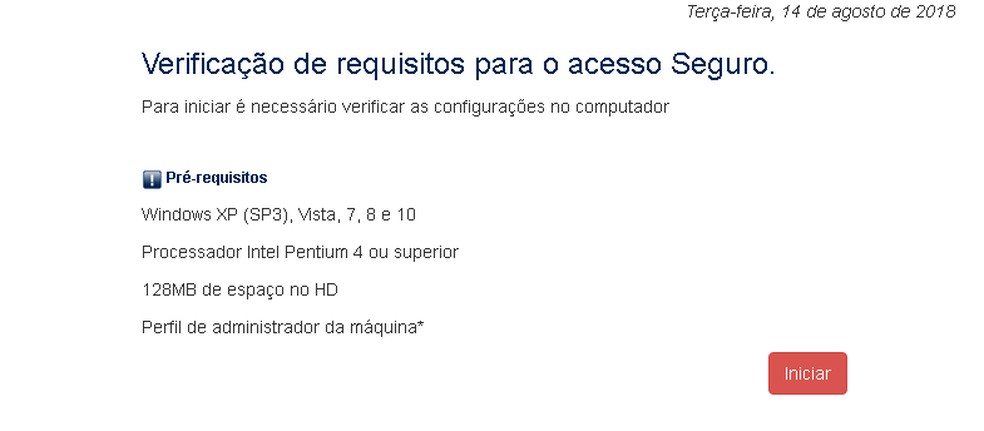
Disguised as a security module, CamuBot requires administrator privileges as a prerequisite for installation Photo: Divulgao / IBM X-Force
CamuBot runs on the victim's computer as soon as the installation starts, behind the fake application interface. To circumvent antivirus and firewalls and appear safe, the malware, which has administrator privileges, adds itself to the list of approved programs. In addition, the name of the downloaded file and the website URL change with each attack.
After installation, the user is redirected to a phishing website that looks like an internet banking portal. The attack is complete when the victim logs into his bank account, unknowingly handing over his credentials to the attacker.
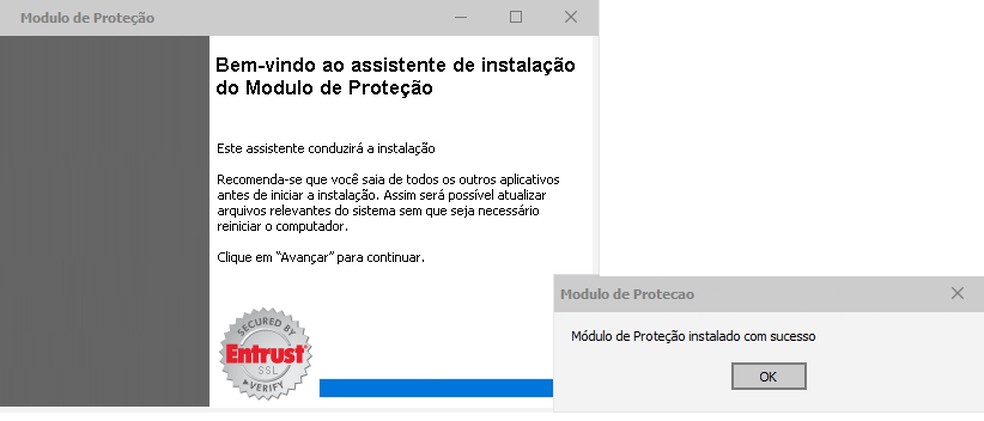
While the installation of the fake security module is complete, the virus lodges on the victim's computer Photo: Divulgao / IBM X-Force
Another worrying differential of CamuBot is its possibility to circumvent biometric authentication, a protection feature considered reliable. According to IBM X-Force, the virus is able to search for and install drivers for authentication devices in two steps, causing victims to activate remote access. This allows the attacker to intercept single-use passwords and carry out fraudulent transactions without raising suspicion from the bank.
Currently, CamuBot targets corporate account holders in Brazil. As the attack is widespread over the phone, suspect calls and ask the alleged caller of the bank to call you back. Then, call your bank with the number you have on your card and inform them about the unsolicited call.
So far, IBM X-Force investigators have not detected CamuBot attacks outside the country, but warn that this could change.
