A new type of Android ransomware is being spread by malicious links in SMS messages and online forums such as Reddit and XDA Developers since July 12. In general, the infected e-mail address invites the user to install a sexual simulation game, which hides malware capable of encrypting the victims files. To unlock documents, cybercriminals ask for a bitcoin payment. The discovery was announced on Monday (29) by security company ESET.
Telegram changes the way of entering the app after account invasions in Brazil
New ransomware attacks Android users via SMS messaging Photo: Luciana Maline / dnetc
Want to buy a cell phone, TV and other discounted products? Meet the Compare dnetc
The ransomware has been dubbed Android / Filecoder.C and marks the end of two years of decline in malware detections for Google's operating system. According to ESET researchers, most malicious links are shortened, which distorts domains of suspicious origin.
Attracted by pornographic material, victims are forced to manually install the infected application. When run, the app displays the promised content on the source link in general, a sex simulation game. Behind the game's interface, Filecoder.C is activated, initiating command and control communications and implementing encryption mechanisms.
Another ability for ransomware to access the user's complete contact list and send malicious links via SMS. The messages include the recipient's name and alert potential new victims that their photos are being used in the sexual simulation game. Filecoder.C even customizes the text language to the default language of the infected phone.
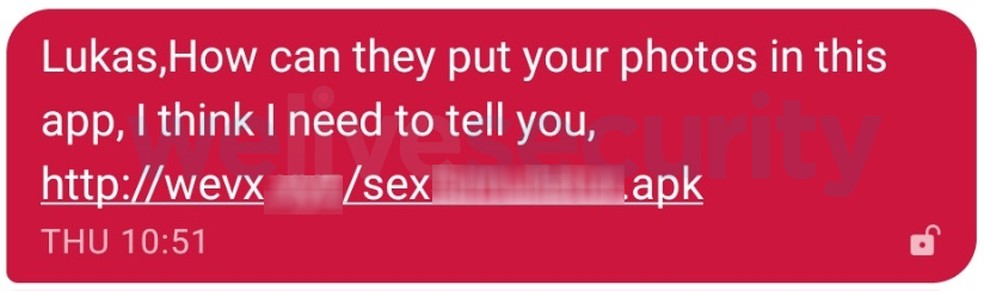
Message displayed to Filecoder.C victims warns of alleged use of personal images Photo: Playback / ESET
Criminals ask for bitcoin payment to return files
Ransomware encrypts various file types, including DOC, PPT, and JPEG. After encryption, Filecoder.C displays a note requesting payment of a certain amount in bitcoins to decrypt the files. The alert warns that data will be lost after 72 hours and also informs you that deleting the application will not undo encryption.
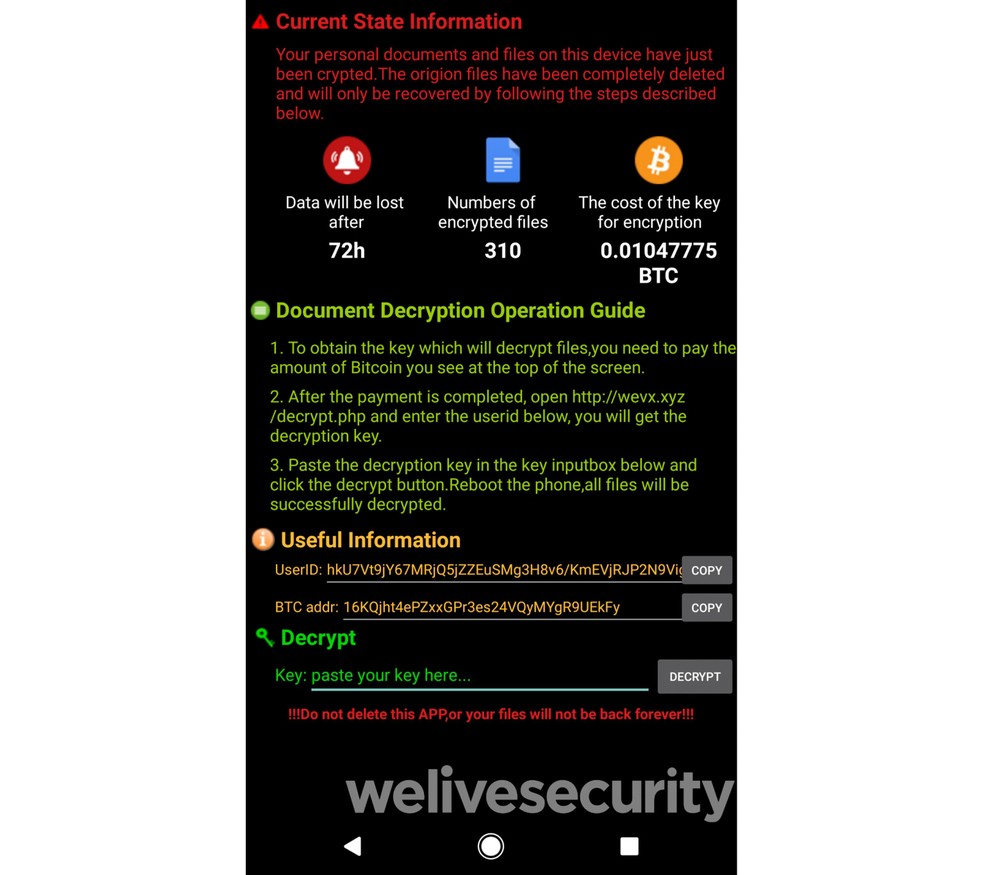
Ransom note issued by ransomware warns that uninstalling the app does not cause encryption Photo: Playback / ESET
It is true that if the victim removes the application, ransomware will not be able to decrypt the files as indicated in the ransom note. Also, according to our analysis, there is nothing in the ransomware code to support the claim that the affected data will be lost after 72 hours, says the ESET publication.
For experts, narrow targeting and failures in campaign execution and encryption implementation make the impact of the new ransomware very limited. "However, if operators start attacking larger groups of users, the Android / Filecoder.C ransomware could become a serious threat," they warn.

How to Remove Virus on an Android Phone
