For Rui Duro, when he is at our workplace, there is a whole infrastructure of protection and formalisms. At home, we will apply the informality of being in pajamas and slippers to work, but we ended up adapting this neglect in remote work, with regard to safety precautions.
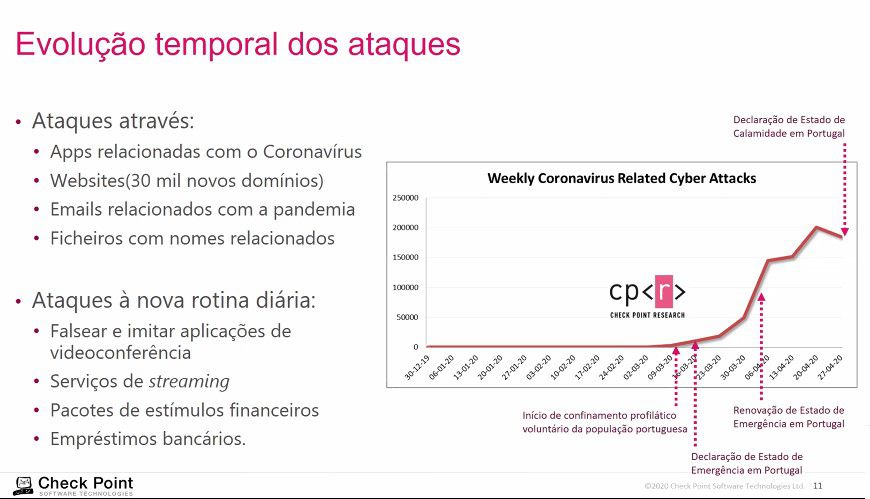
Regarding the temporal evolution of the attacks, there are more and more Coronavirus-related apps, more than 30 thousand new domains, as well as emails and files related to the pandemic, since late March 2020. Attacks new daily routine are linked to the distort and imitate video conferencing applications, streaming services, financial stimulus packages and bank loans that users should be aware of.
Check Point reports that 71% of professionals realized the increase in threats due to COVID-19, but due to the current situation, 95% of companies have additional security challenges. Among the concerns are the VPN configuration for secure remote access; the scalability of the solutions used; as well as the use of software, services and tools not tested and not authorized by IT departments.
Despite considering that phishing itself is not a concern, Rui Duro points to the danger of the doors it opens to attacks. This is because when confidential information is stolen and is a way to make ransomware, the data can also be sold on Darkweb. Most of the thefts are not even to be used, but rather sold, giving as an example that a patient's health record, with his personal data, can be worth much more than a credit card, as a false identity can be built of an individual.
Rui Duro says there was a lot of noise around Zoom, whose exposed vulnerabilities forced the company to work to correct them. The problem, for the specialist, lies in the people and organizations that went to other applications, which, because they have not been exposed, can continue with vulnerabilities that no one knows and be the target of attacks.
It was also mentioned that phishing attacks are made in association with brands, especially those that are most used in this period at home. Apple was the main player, with 10% of the attacks, followed by Netflix with 9% and Yahoo with 6%. Most attacks are made by web pages, which is equivalent to 59%, followed by mobile devices with 23% and finally, via email, with 18% of cases.

And for the operating system that has the most known vulnerabilities, Apple's iOS, although the most vulnerable is Android. Rui Duro explains that in the Apple operating system there are daily updates, several times a day, he says, while there is not so much concern in Android, being the target of more attacks.
To prevent attacks in the future, Rui Duro highlights the importance of educating users and teaching them to distrust addresses and social networks. I was educated to never accept sweets or rides from strangers, the expert compares, referring that when we go to the virtual world these principles must be taken, trying to understand when the website is malicious or not. We must, of course, be wary of promotions that are very attractive.
This is what Check Point considers that the return to companies should be done, the need to clearly segment access to information, protect mobile equipment, train employees and prevent as many cyber attacks as possible, optimizing security tools .
Back to work, we need to segment the access information clearly. Protect mobile devices, train employees and guarantee to prevent cyber attacks. Use secure communication systems and optimize cybersecurity tools. Websites like "Have I been pwned" can help you to guess if the email address is compromised.
Editorial note: The article was updated at 13:00 with more information.
