As we have commented several times, the macOS vulnerable to certain types of attacks, especially malware that uses email or websites to install. Despite constant improvements in system security, crackers constantly develop tools that are increasingly similar to tasks that are commonly performed by the user to try to hack and remotely access the Mac.
In one of these attacks, access to the system is through a URL scheme that, in Safari, involves some actions by the user to be installed, as reported by the blog. Objective-See. According to the web security researcher Patrick WardleSuch a scheme involves creating a website that automatically downloads a .zip file to the user's computer.
Because it is a signed software, therefore supposedly “safe”, Safari runs it immediately after downloading it, if the option “Open files after transfer” is enabled in the browser preferences. When installed, packages containing custom URLs (used to manipulate macOS) are registered in the system. So when Safari is open, the software code that the user accidentally just installed will activate the URL handler.
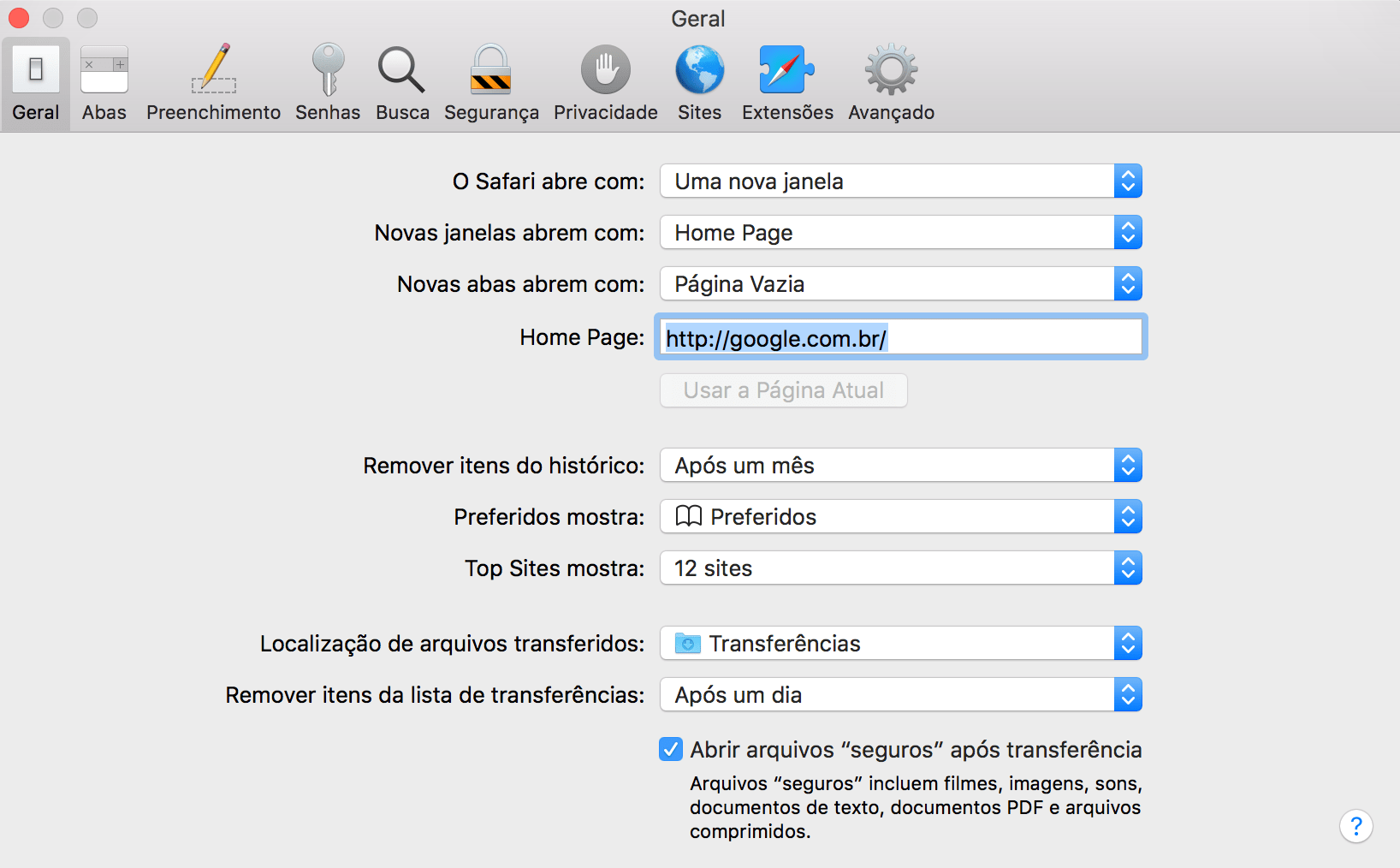
At the next stage, when the infected web page opens, Safari displays a popup window. At this prompt, the user may allow the newly installed application on the Mac to open the file through the Advanced Packaging Tool (Advanced Packaging Tool, or APT).
Both macOS and iOS use APT for a variety of tasks, whether it's opening a PDF document after downloading (which will run the Preview app by default), or then when a web page, usually from Apple itself, runs iTunes or the App Store (on Mac or iPhone). In this case, the popup displays actions that are controlled by the attacker and therefore are easily changed to trick the user into clicking "Allow" (Allow) to open malicious software.
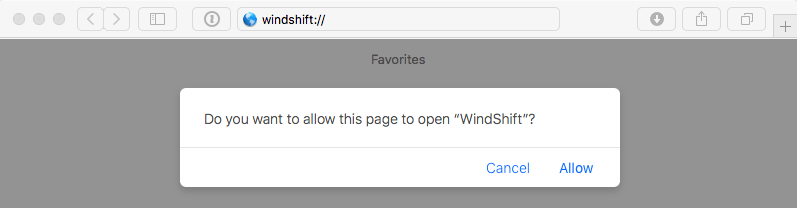
The Mac will display another security warning before opening the software permanently. This time, Gatekeeper alerts the user that the application has been downloaded from the web, so it may not be safe. However, just like the URL scheme, the file name can also be changed, manipulating / influencing user decision.
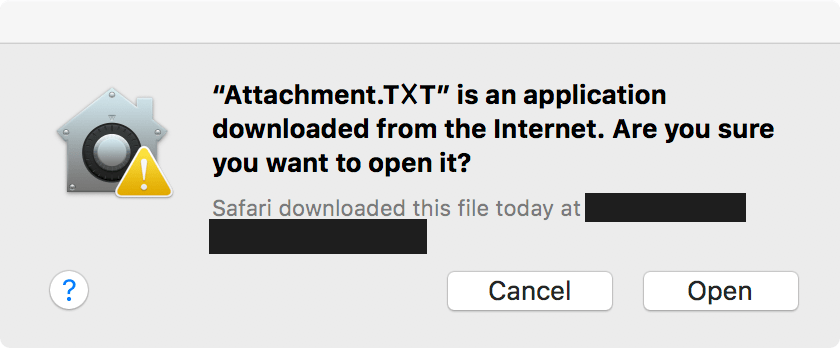
While it's not necessarily a new security flaw besides requiring some user interaction, the best protection that macOS users can do is to disable automatic unzipping of downloaded files (if you use another browser, you don't have to worry about it) . To do this, click on "Preferences" in the Safari menu, choose the "General" tab and uncheck the "Open 'secure' files after transfer" checkbox.
And be careful, as always, where you download your software from.
via 9to5Mac
