Ransomware is a type of virus that makes it impossible to access your data and is only released upon rescue. Learn how to permanently delete from your PC
The epidemic of viruses that encrypt files and extort money from users has gone global. One of the first was the ransomware WannaCry, launched in 2017, using SMBv1, a protocol that helps PCs communicate with printers and other devices connected to the network. Their clones and modifications followed. What if your files are affected by this plague? You are unlikely to be able to decrypt the files, even after paying a ransom. The only option to find an alternative is:
- Restore data from backup;
- Extract files from emails;
- Search for contacts and information in messengers.
 The Ransomware virus attacks mainly through printers and other devices
The Ransomware virus attacks mainly through printers and other devicesDevelopers of software, such as Microsoft it's the Windows 10 do not have a solution to the problem, making it the most effective option to restore the database SQL Server from the last backup. However, what if the server cannot be restored from the backup? What to do if the ransomware also encrypted the backup?
Ransomware virus bug
Virus spread due to various bugs in programs, operating systems and through social engineering. However, viruses are programs, so they also have bugs and vulnerabilities. The virus ransomware, for example, you need to encrypt the maximum number of files quickly. For small files, such as Excel, Word, Power point, Project, AutoCAD, CorelDRAW, and other data files, the fast encryption process.4
What if it happens if a virus finds a long file, like a FoxPro or Microsoft Access database? In this case, the virus usually encrypts the beginning of the file and moves it to the next one on the disk.
This gives a little hope to users. Microsoft SQL Servers save files to files MDF and NDF. The size of these files is impressive: gigabytes and terabytes. For archiving, wide disks are used, usually based on RAID controllers. Each file starts with a small header, followed by large amounts of service information for quick access to data, service information describing user data and the like.
In most cases the virus encrypts most of the service data in files MDF and NDF. Still, the pages containing data in the file remain unencrypted.
SQL Server Indirect Data Recovery
There are some sophisticated tools that can read data and join all data pages and blocks if the service information is no longer available due to the virus attack.

Still, the next step is to look for the tool (utility, service, or other method) that can analyze data in files MDF and NDF; the recovery utility can do that for damaged database Microsoft SQL Server. They solve similar problems under the same initial conditions when a part of the database file is missing or corrupted.
The most accessible and simple utility for these purposes is Recovery Toolbox for SQL Server. O software was developed more than 10 years ago from the first versions of the Microsoft SQL Server (6.5, 7.0, 2000) to the most recent (2017, 2019).
 The most accessible and simple utility for these purposes is the Recovery Toolbox for SQL Server.
The most accessible and simple utility for these purposes is the Recovery Toolbox for SQL Server.Recover the SQL Server database after the ransomware virus attack
Once Recovery Toolbox for SQL Server it was developed for only one purpose (to recover damaged Microsoft SQL Server databases), it contains only a few configurations. The utility is made in the form of a step-by-step assistant, and at each stage, the user does a few simple actions:
- Select the encrypted MDF file;
- Choose a recovery method and location to save recovered data;
- Select data to be saved;
- Starts data recovery and backup.
In the initial stage, the utility reads and analyzes the encrypted database of SQL Server for a long period; this is the most crucial stage of the program's operation. The larger the size of the source file and the complexity of the data, the longer the period the program will run at this stage. If there is a powerful server available, it may take a day for the program to go through files of size 1-5 Tb.
Everything that was restored from the archive MDF encrypted form presented to the user in the form of convenient tables and lists within the Recovery Toolbox for SQL Server. The user can browse through the pages containing data, tables, functions defined by the users and procedures.
If the file MDF has been successfully analyzed, then the lists and tables on the program's 2 page are not empty. Otherwise, there is nothing to see and nothing to pay since the demo version of Recovery Toolbox for SQL Server free.
If the analysis of the encrypted file was successful, then you must choose how to save the data:
- Like SQL scripts in several separate files;
- Alternatively, export data to a new database Microsoft SQL Server.
Attention: when restoring a database from SQL Server after a virus attack ransomware, there is a chance of losing some of the data; also, data integrity can be compromised. As a result, primary and foreign keys are unlikely to work; this is revealed at the stage of execution of SQL scripts with Primary Keys and / or Foreign Keys after the data has already been imported into the database. Scripts with primary keys will not be executed or will be executed with errors.
The script execution sequence SQL when exporting data to a new database:
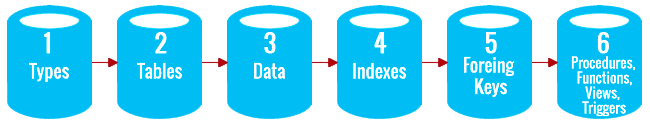
This sequence of scripts presented in the installation file .bat, that Recovery Toolbox for SQL Server saved in the folder with all other scripts SQL. Just run this file with the necessary parameters (Server name, database name, username and password) on the command line. You may have to run this script several times to import the data into the most complete database.
Recover the database without payment
Now if a virus ransomware encrypted your database SQL Server, then you can try to recover the data without payment. To do this, you must:
- Restore data from backup;
- Extract data from .MDF / .NDF files using Recovery Toolbox for SQL Server as SQL scripts;
- Import data from SQL scripts into a new database SQL Server.
Managed to eliminate the virus ransomware of your life? Leave it in the comments!
