Microsoft and Intel are exploring a new approach to classifying malware: converting it into images before analyzing it. The idea that technology is able to better detect the threat, transforming the codes into images so that a deep learning system can study them. It will also be possible to detect malware even before it is run.
In a statement, Microsoft and Intel explain that the approach converts the binary form of a file made up of pixels into an image with varying dimensions. Then, the system is able to determine what infected the file if malware is detected.
In practice, the technology dismantles the code without the need to run applications or monitor the runtime behavior. In this way, it produces metadata about a file and allows the threat to be identified even before it is executed.
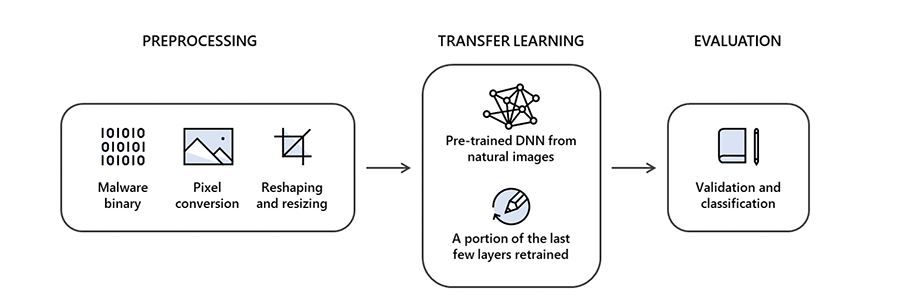
The results of the system were published in a paper, with both companies confident that this is just one of the strategies that can improve cybersecurity. So far, the approach called static malware-as-image network analysis (STAMINA) has proven to be quite effective, with just over 99% accuracy in classifying malware. On the other hand, the false positive rate was 2.6%.
Despite the success of the system, the truth is that technology also has its limitations. STAMINA works much better for small files than for larger documents.
The information released at a time when, in the middle of the pandemic, a cybersecurity report from Microsoft revealed that computer attacks related to COVID-19 have been recorded in all countries of the world. According to the document published in mid-April, more than 60,000 emails and 18,000 malicious URLs and IP addresses are used every day using the public health crisis as a way to draw users' attention.
