After confirming that it was the victim of a coordinated social engineering attack that gave rise to an advanced cryptocurrency fraud scheme, Twitter now reveals the first details of the investigation into the incident.
The company led by Jack Dorsey reports that 130 accounts have been attacked, including verified pages of medical figures and technological giants. In all, hackers were able to change passwords for 45 accounts and make Tweets through them, in addition to stealing data from 8 pages.
In a post on its official blog, Twitter explains that hackers were able to access private messages and information such as phone numbers and email addresses of the 8 accounts targeted through the social network's data archiving feature. According to the company, the accounts in question were not verified pages.
The company confirms that the hackers managed to manipulate a small group of employees and used their credentials to access the computer systems and internal tools. By answering again, the question remains how the hackers managed to get in touch with the employees and get them to give the information they needed.
Amid theories of bribery and kidnapping on employees' accounts, The New York Times advances that the attack was already being planned by a group of hackers from the OGUsers forum. Users of the online community are engaged in the business of buying and selling highly coveted accounts, usually with very short addresses.
According to the publication, two hackers in their 19s and 20s, known only to usernames lol and ever so anxious came into contact with another user of the forum called Kirk, a figure seen by many as those who were in charge of the attack.
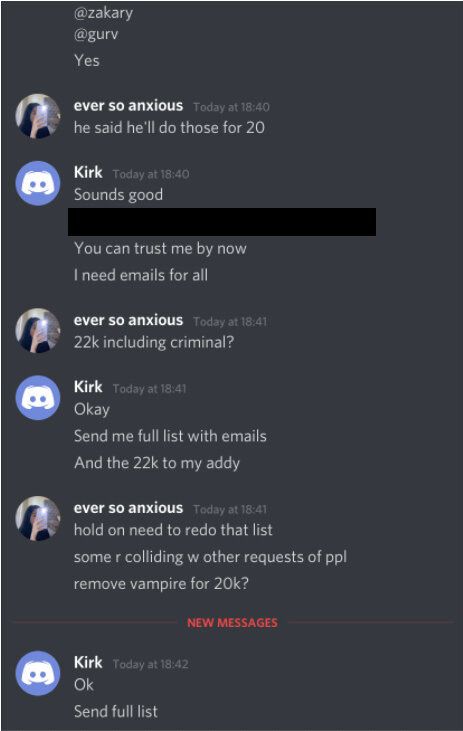
Apparently, hackers were complicit in the attack, serving as intermediaries in the process of selling and buying accounts. publication lol and ever so anxious indicated that Kirk was able to obtain access credentials to Twitter's computer systems and tools through a message posted on the company's Slack channel.
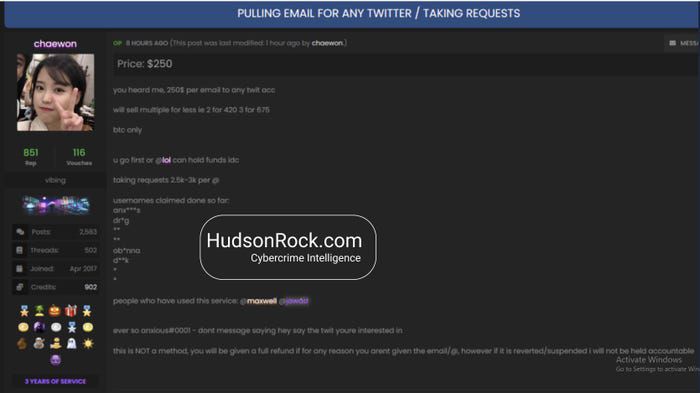
Links to the OGUsers forum are also supported by Reuters, well-known researcher Brian Krebs and Hudson Rock. In an interview with Business Insider, the cybersecurity company reveals that, days before the attack on Twitter, a user who takes the name Chaewon advertised his services on the forum, indicating that he could change the email address of any account for 250 dollars and give full access even for a price between 2 thousand and 3 thousand dollars.
For now, although it does not confirm whether any of the advanced hypotheses describe the reality of the situation, Twitter says it will continue to investigate the case and that it will take tighter measures to mitigate the consequences of the attack, including restoring users' confidence.
We are aware of our responsibilities to the people who use our service and to society in general. We are embarrassed, disappointed and, most of all, we apologize, underlines the social network.
