Apple is not at peace with the press and its hiprboles. A partial leak of the source code of one of the most important security components of iOS, the iBoot, was reported extensively throughout the day, motivated by the court order filed by the company to GitHub for the removal of the material after it was discovered last night.
According to experts, the material disclosed is unduly true, but in the new one: last year, it had already appeared in a publication on Reddit, which was also dropped after the intervention requested in court. It could be the biggest leak in history, as some vehicles are saying but no.
What does iBoot?
IBoot is one of the components of the secure chain of boot of Apple's operating systems primarily iOS, but there are variations of it on watchOS and tvOS. To explain its operation, it is necessary to understand a little about how this chain works.
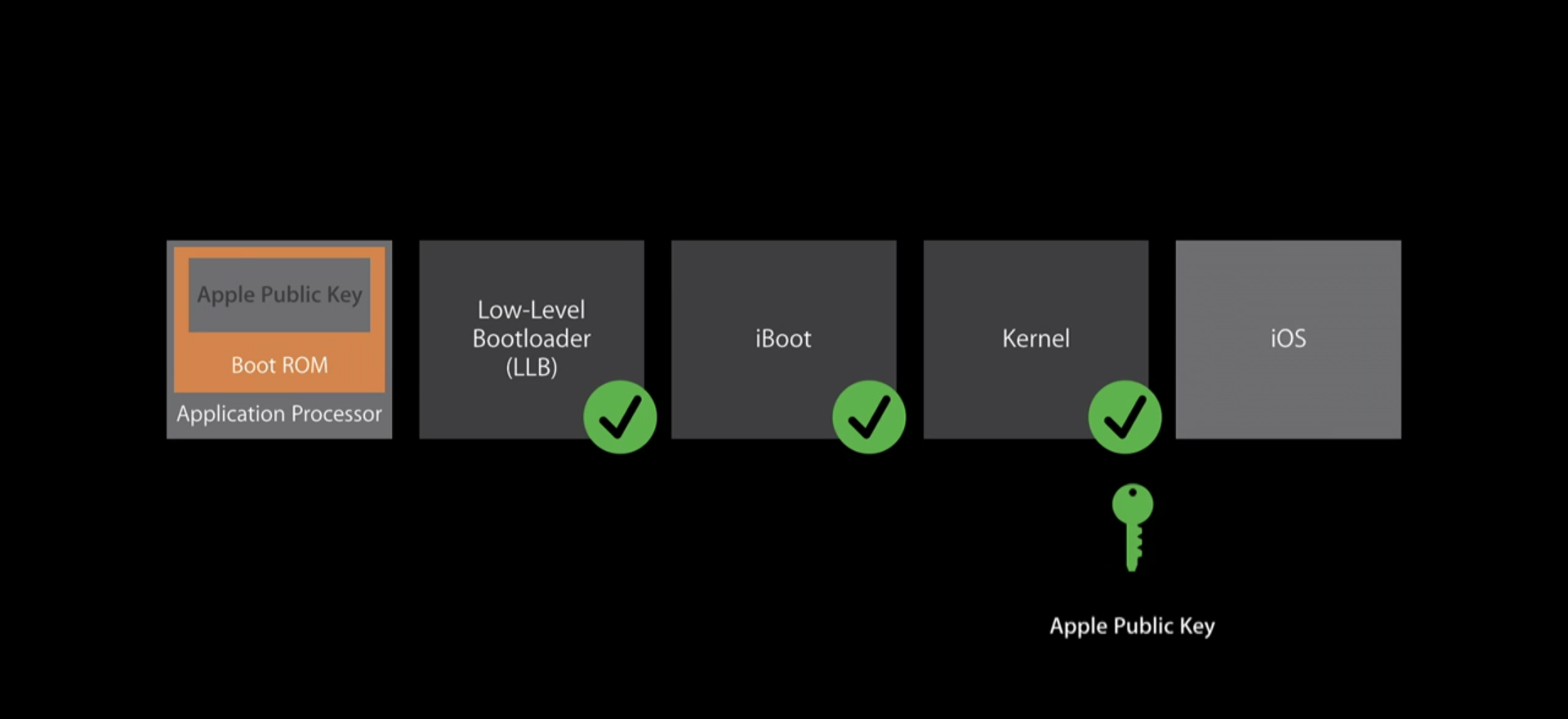
According to Apple, for an iPhone or iPad to be initialized, the processor executes instructions present in memory that are only read-only (ROM), that is, as explained in the platform security document, they were shipped on the chip during its manufacture and they are implicitly reliable. In the middle of this path, these instructions validate the digital signature of all components of the device and the iOS installation itself; when these integrity tests pass successfully, iBoot is then asked to validate the kernel of the system and initialize it.
The function of iBoot is very specific and depends on all tests performed in the initialization chain to be considered. In other words, a component that cannot initialize a device if its instructions loaded in ROM do not validate its authenticity, as is done throughout the chain.
IOS also interacts with Apple servers for its updates, so iBoot is not immutable; in the case of the leak released today, the source code of iBoot corresponds to what was distributed on iOS 9, between 2015 and 2016.
What the experts said
At first, the leak of the source code was partial: there are no files that would be used to compile it into a version capable of being exploited during its operation. However, documents with relevant information from iBoot and other components that boot iOS devices were also found.
This is the SRC for 9.x. Even though you cant compile it due to missing files, you can mess with the source code and find vulnerabilities as a security researcher. It also contains the bootrom source code for certain devices…
– Apple External (@Apple_External) February 6, 2018
This is the SRC for 9.X. Even though you can't compile it due to missing files, you can still tinker with the source code and find vulnerabilities as a security researcher. It also contains the source code bootrom for certain devices
a full plate for the community that works in jailbreaks of appliances. For years, they have worked primarily on vulnerabilities to produce utilities that break Apple's protection against running code obtained from outside the App Store. Furthermore, given the company's past controversy with certain governments that sought to break the native iOS protections for surveillance purposes (understand as you wish), it is clear that the interest in this type of information is extremely high, regardless of its creation or how recent it is. .
What is not clear, however, is how dangerous this is for users compared to what we have seen before. This is where the margin lies to make such a news a tragedy. However, breaking the security of any iPhone or iPad, although it is unwanted and always highlighted by the press, is nothing new.
In the past, hackers have been successful in exploiting flaws of this nature through other methods, without direct access to Apple source code and confidential documents jailbreaks nothing more than just that. When a user applies any of them to their device, they are not only enabling them to do anything: they are also breaking the security of the device in question with a known vulnerability in the bootloader or in other areas, depending on the scenario explored by the attacker.
What a leak like this week's increase is the possibilities for studies on iOS, whose failures due to broken startup components are the best paid in the reward program (bug bounty) that Apple has been on the market since 2016.
Apple Announcement
In response to the leak and its downfall on GiHub, Apple provided the following statement to the MacRumors and some other sites:
The old source code from three years ago appears to have been released, but by design, the security of our products is independent of the protection of our source code. There are several layers of hardware and software protections integrated into our products and we encourage users to upgrade to the latest versions and benefit from the latest protections.
Among these layers, in addition to those mentioned at the beginning of this article, is also the safe enclave (Secure Enclave) that protects users' biometric data on device processors, for example. It is worth remembering that iBoot itself is capable of being updated like several other iOS components, in case any security problem affecting users is identified.
It certainly does. It is expected that Apple will increase its comb in capturing these errors and fix them preferentially, faster than the bugs that still freeze our devices today and the bizarre that are appearing in macOS.
